Home » Course Layouts » Free Course Layout Udemy
This course covers a number of advanced “selected topics” in the field of cryptography
0
2
English
English [CC]
- Learn basic syntax that can apply to any language.
- Learn what is a programming language and the basic concepts for beginners.
- Understand what is Javascript in it's truest form.
- Know the basic syntax of Javascript.
- Know some hidden quirks in Javascript.
Description
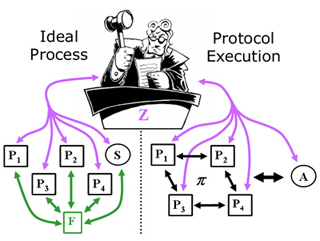
The first part of the course tackles the foundational question of how to define security of cryptographic protocols in a way that is appropriate for modern computer networks, and how to construct protocols that satisfy these security definitions. For this purpose, the framework of “universally composable security” is studied and used. The second part of the course concentrates on the many challenges involved in building secure electronic voting systems, from both theoretical and practical points of view. In the third part, an introduction to cryptographic constructions based on bilinear pairings is given.
Course content
- Overview of the Course Unlimited
- The Non-Concurrent Unlimited
- The Universally Composable (UC) Security Framework Unlimited
- UC Commitments: Motivation. Unlimited
- UC Zero Knowledge from UC Commitments Unlimited
- Universal Composition with Joint State. Unlimited
- Authenticated Key Exchange and Secure-Session Protocols. Unlimited
- “Introduction to Electronic Voting” Unlimited
- “Verifable Mix-Net Voting” Unlimited
- “Neff (VoteHere) Voting Scheme” Unlimited
- “Chaum’s Election Scheme” Unlimited
- “Pairing-Based Cryptography” Unlimited
N.A
- 5 stars0
- 4 stars0
- 3 stars0
- 2 stars0
- 1 stars0
No Reviews found for this course.